Phishing: How to recognize fraudsters and protect your data
Fake emails, deceptive links, stolen passwords — phishing has become the internet’s primary trap. While scammers constantly refine their schemes, they can be identified. How to avoid getting caught, and what to do if you’ve already fallen victim? Verify emails, evaluate risks, and respond appropriately.
Phishing ranks among the most prevalent social engineering schemes used by fraudsters. This method steals user credentials (logins and passwords), bank details, SMS codes, device access, and other sensitive information through fraudulent links and file attachments.
As we outlined in our previous article “Personal data theft: How to protect yourself in the digital world,” hackers frequently employ this fraud type because it exploits human psychology — meaning no internet user is completely safe from phishing. This makes understanding basic protection rules absolutely essential.
How to avoid becoming a victim of phishing
Phishing can appear in SMS messages, social media posts, fake websites, and emails. Remember this when encountering unexpected messages, link requests, or prompts to enter personal data. Always verify the source and avoid rash actions.
Let’s examine key counter-tactics using email as an example. Messages containing third-party links or attachments demand extra scrutiny. Analyze emails for phishing by asking:
1. For emails from unknown senders, consider:
- Was I expecting this message?
- Is the request logical?
- Do I recognize the sender?
- What are the potential consequences of complying?
Examples of phishing emails:
• “Your account has been blocked! Follow the link to unblock it immediately.”
• “You have been awarded a bonus – download the document to receive it.”
• “Your bank card has been blocked – confirm your details.”
2. Verify the sender’s address. Check if you recognize the sender and look for spelling errors in the email address.
Phishing emails often impersonate reputable companies (banks, social networks, government agencies) but contain telltale flaws:
• Letter substitutions: supp0rt@bank.com (using the number 0 instead of the letter o)
• Fake domains: emails supposedly from “Google” sent from google.support@mail.com
• Random mailbox names: no-reply-service9342@gmail.com
Verification methods:
- Hover over the sender’s name (without clicking) to view the actual email address
- Remember: Official organizations never use free email domains (@gmail.com, @yahoo.com)
3. Scrutinize the sender’s full name.
Even legitimate-looking emails may have fabricated sender names:
•Name-address mismatch: “From” shows “Google Security Service” but uses security2024@scam.com
•Fake titles: “Google Security Director” from google-support@yahoo.com
Verification steps:
- Always cross-check the name with the email address
- Genuine corporate emails typically include an employee’s actual name
- Examine other details: spelling errors, odd punctuation, incorrect dates or locations may reveal phishing
- When in doubt, contact the supposed sender through verified channels
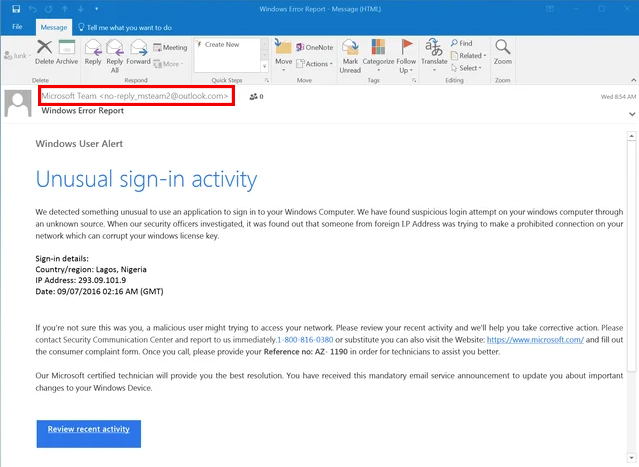
4. Do you recognize the website in the email?
Scammers mimic real websites, but the URL exposes the fraud:
• Legitimate: https://www.google.com
• Fake: https://google-security.com or https://google.login.secure-site.com
Verification methods:
- Type the website address manually instead of clicking email links
- Check for HTTPS and the padlock icon (though this doesn’t guarantee safety)
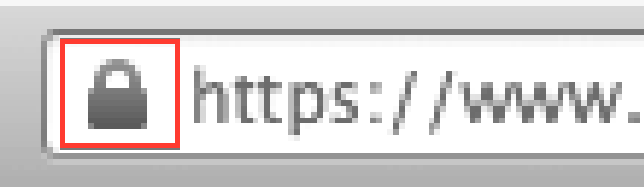
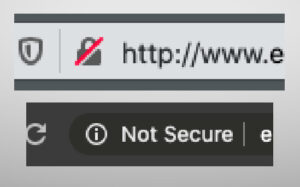
Closed lock = secure page
Crossed-out lock = potentially unsafe connection
5. Watch for shortened URLs
Cybercriminals use services (bit.ly, TinyURL) to mask malicious links. Example: bit.ly/3xY7zKk actually directs to hackers.com/steal-your-data
How to verify:
- Hover over links (without clicking) to preview the real URL in your browser’s status bar
- Use link-expanding tools like Unshorten.it
6. Avoid downloading or opening files when:
- You weren’t expecting this file from the sender
- You don’t know the sender
- You’re unsure which program opens the file
7. Never enable macros from untrusted sources in office applications (A macro is a programmed sequence that automates tasks in programs like Excel or Photoshop).
Macros in Excel/Word are frequently exploited by hackers to deliver malware. Typical attack example: You receive “Reconciliation_Act.xlsm” demanding you “enable macros to view content.” Once enabled, a Trojan infects your system, granting attackers access to your data.
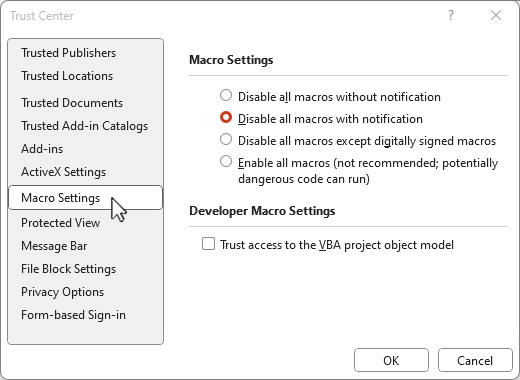
Protection measures:
- Set macros to be disabled by default in Office settings
- Request alternative formats (PDF, images) when files are work-related
8. If you identify a phishing email:
- Do not click any links
- Do not copy link addresses
- Do not open or download attachments (this applies to mobile devices too)
- Do not download images from unknown senders
- Do not forward the email to colleagues
9. Enhanced security measures:
- Activate two-factor authentication for critical accounts
- Install antivirus software — it warns about dangerous links
- Utilize website security scanners (like Quttera or VirusTotal)
- Add anti-phishing browser extensions (such as Avast Online Security)
- Study real-world cases in phishing databases (e.g., PhishTank)
What to do if you’ve fallen victim to phishing?
- If you suspect compromised data: Change it immediately.
• For lost/stolen devices (phone/laptop):
– Contact your mobile provider to block the SIM card
– Call your bank’s support to freeze payment cards
– Initiate remote data wipe on the device
• For hijacked accounts:
– Use account recovery options (backup email/phone/security questions)
– Change passwords on all related accounts
- If you clicked a phishing link:
– Never enter account credentials or banking details
– Immediately close the webpage without taking any actions
– Run a full antivirus scan to detect potential malware downloads - If you submitted data via phishing:
– Stay calm and act swiftly
– For compromised card details — block the card instantly via your banking app or your bank’s hotline
– For exposed account credentials — change your login password immediately
Vigilance and basic security knowledge help prevent data loss. Remember: phishing exploits inattention. Always pause and verify details carefully! The ultimate defense against phishing is maintaining healthy skepticism and exercising caution online.