Personal data theft: how to protect yourself in the digital world
In the digital age, personal data leaks are becoming increasingly common, while fraudsters’ methods grow more sophisticated. Phishing, vishing, skimming, and other schemes enable attackers to access confidential information, potentially leading to serious financial and psychological consequences. How can you protect your data and minimize risks? Let’s examine this in the article.
What is personal data and how is it stolen
Personal data essentially constitutes any information relating to an identifiable individual (the personal data subject). Various pieces of information that, when combined, can identify a specific person also qualify as personal data. This includes:
- Full name, date of birth, and other passport details
- Exact residential address
- Information about relatives, health status, and income
- Photographs or videos enabling personal identification
- Phone numbers, email addresses, and similar contact details
It is worth noting that data cannot be considered personal if it doesn’t allow identifying a person without additional information. Simply knowing a person’s name doesn’t constitute personal data. Similarly, a phone number alone isn’t personal data, but when combined with the owner’s full name, it becomes personal. Therefore, if a combination of data points can identify a specific individual among others, such information qualifies as personal data.
Data theft refers to the unauthorized acquisition of digital information (bank details, passwords, passport data, etc.) for illegal purposes. Attackers may alter, delete, or block access to this information, as well as sell it or use it for fraudulent activities. While companies were previously more vulnerable to leaks, ordinary users now face equal risks. Fraudsters only need a small amount of data to gain access to accounts, bank cards, and other personal information. Let’s examine the primary methods of data theft.
1. Phishing (derived from “fishing” and “password”) is a type of internet fraud aimed at stealing identification data: passwords, card numbers, bank accounts, and other confidential information. Typically, a phishing attack involves creating fake websites that mimic pages of popular companies: banks, online stores, streaming services, etc. Hackers rely on users failing to notice the deception and entering personal data on these pages: card details, login credentials, phone numbers. If successful, the fraudsters obtain this sensitive information.
The fundamental challenge with phishing is the absence of absolute protection against visiting counterfeit sites. The human factor proves decisive in these cases, as even technology giants remain vulnerable when employees fail to recognize the scam due to carelessness.
The consequences of phishing attacks can be far-reaching. A notable example occurred in 2014 with the hacking of Sony Pictures Entertainment, one of the world’s leading film studios. The hacker group Guardians of Peace researched employee profiles on LinkedIn and sent emails containing malicious files. Once installed on corporate computers, the malware enabled months of surveillance and remote device control. The hackers subsequently leaked unreleased films and stole extensive sensitive data including employee and family member personal information, internal emails, salary details, and unreleased film copies — totaling over 11 TB of compromised data.
2. Smishing (smishing = SMS + phishing) is essentially phishing distributed via SMS or instant messages rather than email. Fraudsters typically send messages about fictitious problems — a delayed package, unpaid bill, or blocked account — urging recipients to click a link. Victims are then directed to fake applications or websites mimicking legitimate services that aggressively prompt them to enter sensitive data.
3. Vishing (from voice phishing) is telephone fraud where attackers pose as organizations (banks, service providers, government agencies) to convince victims they must urgently share confidential information (codes, passwords, details) with fake security personnel. They deliberately create false urgency and threats to provoke thoughtless compliance.
4. Skimming (from “skim” — to slide, to read quickly) involves stealing bank card information during transactions. Criminals may tamper with card readers to record data, install recording devices on ATMs, or collude with dishonest merchants to capture customers’ card details.
5. Impersonation fraud occurs when criminals gain victims’ trust to extract money, information, purchases, or even money laundering assistance. Common tactics include posing as law enforcement or relatives.
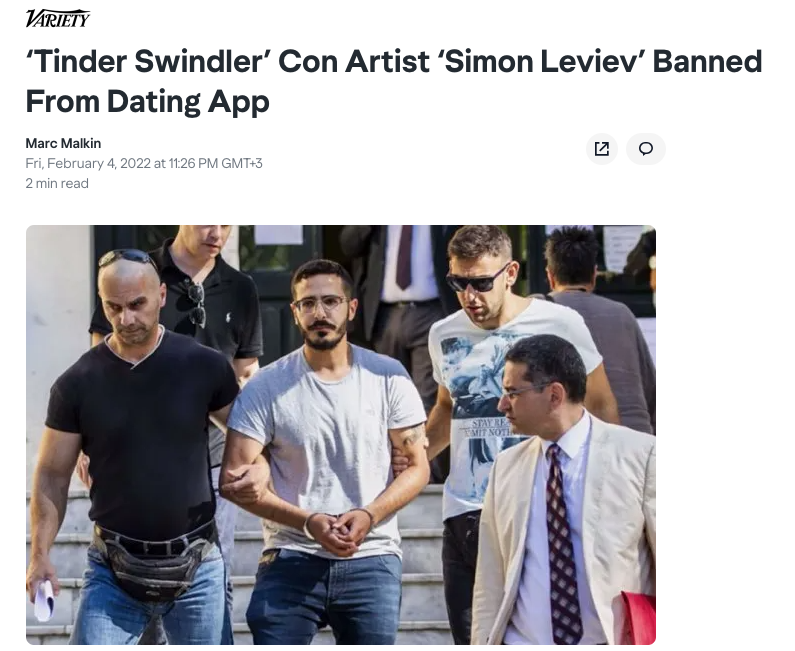
A notorious example is the “Tinder Swindler” case, where Shimon Hayut posed as a diamond magnate’s son on dating apps, gained women’s trust, then defrauded them of millions by fabricating life-threatening emergencies.
6. Jacking and public Wi-Fi. Many public Wi-Fi networks remain vulnerable to hacker attacks, enabling unauthorized access to users’ personal information. Fraudsters may also employ jacking — a USB charging scam where malware infects devices connected to public charging stations.
The most common causes of data leaks
Weak passwords. Using easily guessable passwords or repeating the same password across multiple accounts gives attackers access to sensitive data. Poor password management habits — like writing passwords on paper or sharing them with others — also contribute to data breaches.
System vulnerabilities. Poorly designed software applications or inadequately secured network systems create exploitable weaknesses for data theft. Outdated antivirus software similarly presents security gaps that attackers can manipulate.
Downloads from compromised sources. Users risk downloading malware-infected programs from hacked websites, granting attackers unauthorized device access and data theft capabilities.
Physical actions. Not all data theft occurs digitally — some results from physical actions like stealing documents or devices (laptops, phones, storage media). Attackers may also harvest confidential data by shoulder-surfing victims in public spaces.
Human factor. Data leaks are not always the result of malicious actions; sometimes they can occur due to human error. Common mistakes include accidentally sending confidential information or mishandling database passwords. Significant amounts of sensitive data also become exposed through internet searches or social media posts.
10 strategies for protecting personal data:
1. Antivirus. This is software designed to effectively counter malicious attacks. The antivirus can be configured to operate in the background, performing automatic malware scanning and removal.
2. Strong passwords. Most data breaches stem from weak credentials. Follow these guidelines:
- Never reuse passwords. Compromised data circulates indefinitely on dark web markets. Even complex passwords become vulnerable when used across multiple services.
- Use 10+ character combinations. Mix uppercase/lowercase letters, numbers, and symbols, updating them periodically.
- Avoid personal references. Attackers prioritize password guesses derived from known personal information.
- Leverage password generators. Store generated passwords in a secured vault, requiring memorization of only one master password.
- Never store passwords unprotected. Avoid keeping them in device files, self-messages, or synced notes — these are prime targets for attackers.
3. Exercise caution on public networks. Public Wi-Fi networks typically have weak security, allowing anyone on the same network to intercept your data and steal personal information. Reserve public networks for general browsing — avoid shopping or accessing financial apps.
4. Verify website security. Before entering personal data, confirm the site has an SSL certificate. Check your browser’s address bar for a green lock icon, green bar, or HTTPS prefix. Additionally, review the privacy policy, contact details, or verified security seals from trusted providers.
5. Update your OS promptly. Hackers constantly exploit system vulnerabilities to infiltrate devices. Developers address these flaws through updates, making regular system updates essential for security. Updates patch known vulnerabilities and eliminate hacker entry points.
6. Maintain data backups. Though frequently neglected, backups are critical for security. Note that backups stored on the same server as primary data remain vulnerable. For optimal protection, store backups securely, preferably using cloud storage.
7. Avoid oversharing on social media. Review your privacy settings to control message and post visibility. Exercise caution when sharing locations, hometowns, birthdays, or other personal details. Keeping accounts private and limiting access to trusted connections minimizes risks of personal data misuse from accidental disclosures.
8. Secure your wireless networks. Implement password protection or conceal your network from public view. To hide a Wi-Fi network, configure a Service Set Identifier (SSID) to remain invisible.
9. Two-factor authentication. This security enhancement requires dual verification for resource access: typically, a standard password combined with either temporary codes or security questions.
10. Scrutinize links and attachments. Cybercriminals craft sophisticated phishing attempts mimicking legitimate communications from banks, service providers, or official entities. Indicators like spelling errors or unusual sender addresses often reveal fraudulent messages.
Data protection has evolved from recommendation to necessity in the digital age. Implementing strong passwords, two-factor authentication, antivirus solutions, and skeptical evaluation of suspicious communications significantly reduces breach risks. Remember: your digital safety hinges on vigilance. Consistent application of basic security measures creates substantial barriers against unauthorized data access.